
There are at two primary categories of password guessing attacks:
- Dictionary attacks
- Brute force attacks
A dictionary attack is one that tries a set of well-known words that can be used as passwords. Many people use passwords that could be guessed if one knows even a little about that person. This is one reason why network administrators caution users to create passwords that include numbers and a mix of upper and lower case, and no words that could be found in a dictionary. The dictionary attack rolls though a list of the most popular passwords (gathered and traded by hackers), adding some choices related to the user’s families and pets. It can also sometimes try these backwards and forwards. A brute force attack, on the other hand, is like a patient burglar cracking a combination lock. Starting at some combination, it counts patiently up or down until it exhausts all possibilities. By working sequentially through all characters, including upper and lower case letters, numbers, symbols, and spaces, eventually the brute force attack will discover the password.
One way to thwart a brute force attack is to limit the number of possible guesses by any one user within a given period of time. A network administrator may limit the number of times a user can input the incorrect password when trying to access a resource. If, for example, the user enters a password incorrectly five times in a row in one minute when trying to access an ftp server, the account could be locked for ten minutes, or until the user contacts the administrator to resolve the issue. This type of security does not prevent the brute force attack, but it slows it down enough so that the attacker will want to move on to a more accessible resource or network.
Password behaviors
Users will want passwords that are easy to remember, such as their pet’s name, birthdate, or common words from the dictionary. Explain to them that using common words makes a system only slightly more secure than having no security at all. On the other hand, if an administrator allows only machine-generated passwords that are long and hard to remember, the users may write their passwords down somewhere, thus creating another type of security problem. Users must learn how to create passwords that will be difficult to guess and difficult to crack, yet easy for that user to remember. They must also be informed of the risk of leaving passwords where they can be found and sharing passwords with others, including trusted friends, family, or colleagues.
Password Defense
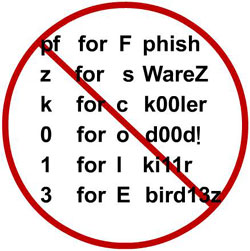
The defense against a dictionary attack is to never use normal words in a password. Use nothing that would appear in a dictionary in any language. The old hacker trick of dropping in a number in place of a similarly shaped letter is no longer considered a defense. It didn’t take long for the password crackers to include alternate spellings. Attackers have also saved successful username and passwords to determine what kind of passwords the users pick. Hacker sites offer such passwords to interested attackers. As the vocabulary of hacked passwords increased, it began to include popular words from foreign languages. Today, it is a good idea to avoid using any word in any language as part of a password.
