Windows user accounts allow multiple users to access one computer or any computer in a network situation. Security is an important aspect for any network or individual computer, so it is important to set up user accounts properly. The first account that is set up during installation is an administrator account. This account should be used to set up computer features and programs and to make administrative changes.
All other accounts that will be used for everyday computing should be set up as standard accounts. The third account option is for a guest account, which is created for users who will only require temporary access to a computer.
Windows requires at least one administrator account on a computer. If you have only one account on your computer, you can't change it to a standard account.
Adding and Removing Users
In order to add or remove user accounts for a workgroup or single computer, follow these steps:
- Step one:
Click on Start → Control Panel → Add or remove user accounts under User Accounts and Family Safety.
If the UAC prompts you for an administrator password, it must be entered in order to continue. - Step two:
Click on Create a new account to add an account, or select an account and click on Delete the account to remove an account. - Step three:
If an account is being created, enter the name of the user account, select a radio button of the account type that is to be assigned to the user, and click Create Account. - Step one:
Click on Start → Control Panel → User Accounts and Family Safety → User Accounts → Manage another account.
If the UAC prompts you for an administrator password, it must be entered in order to continue. - Step two:
Select the specific account that is to be changed and click on Change the account type. - Step three:
Select the radio button of the account type that is to be assigned to the specified user and click on Change Account Type.
Modifying Users
User accounts enable several users to share a single computer or to use any computer is a network setting. Each account will keep the user's unique program settings, operating system settings and preferences, and will also determine which programs can be accessed and changes that can be made to a computer. In order to modify the user account type for a workgroup or single computer, follow these steps:
Users / Security Groups
A user group is a collection of users who have all been assigned the same security permissions. Security permissions control access to system resources, programs installation and removal, and system tasks, User groups are also called security groups. The two most common groups are administrator and standard users, however there are other options:
- Administrator - Administrator users are able to use all available controls such as access to all folders and files; the ability to add, delete, or modify user accounts; install or remove programs, updates, services packs, and fixes; use Safe mode, etc.
- Standard Users - Standard users can access their own files and folders, run programs, install programs that don't require administrative rights, and change their password.
- Backup Operators - Backup operator users are able to access the backup program so that files and folders can be backed up or restored.
- Cryptographic Operators - Cryptographic operator users are able to perform cryptographic tasks.
- Guests - Guest users are only able to access their own files and folders.
- IIS_USRS - IIS_USRS users are able to work on the remote Internet Information Server.
- Network Configuration Operators - Network configuration operator users are abile to install and configure network features.
- Performance Log Users - Performance log users are able to use the Windows Performance Diagnostic Console to locally or remotely monitor performance counters, logs, and alerts.
- Performance Monitor Users - Performance monitor users are able to to use the Windows Performance Diagnostic Console to locally or remotely monitor performance counters only.
- Power Users - Power users are able to backup up, restore, replace, or take ownership of files, install or remove device drivers, and isntall or remove applications.
- Remote Desktop Users - Remote desktop users are able to logon using the Remote Desktop Connection.
- Replicator - Replicator users are able to replicate files across domains.
Add a User Account to a Group
A group of standard users who share the same security rights can be added to a user group, also called a security group. It is important to assign the proper access rights to users; user groups makes this process easier. Grouping users is also an essential time saver for larger networks with hundreds of users. This helps you to avoid granting the same access and permissions to multiple users at once.
To do so, install the Local Groups and Users Snap-in.
Only Vista Business or Ultimate - Windows 7 Professional and Ultimate can perform these steps. Assigning user groups beyond the basic standard or administrator accounts is not an option for Vista Home Basic or Premium nor is this available on Windows Home Basic or Home Premium.
- Step one:
Click on Start, type mmc into the search box to open the Microsoft Management Console (MMC), and press Enter.
If the UAC prompts you for an administrator password, it must be entered in order to continue. - Step two:
On the left pane of the MMC, click on Local Users and Groups. - Step three:
If the Local Users and Groups option isn't available, add it.
Click on File → Add/Remove Snap-in → Local Users and Groups → Add → Local computer → Finish.
Press OK to finish adding the Local Users and Groups option. - Step four:
Double-click the Groups folder. - Step five:
Right-click the desired group, and then click Add to Group. - Step six:
Click Add.
Type the name of the user account. - Step seven:
Click Check Names and then OK until finished.
 Assigning Accounts to Groups in Windows Vista |
 Assigning Accounts to Groups in Windows 7 |
One of Windows XP's security flaws was the fact that it made all users that were created administrator level accounts by default. This was exploited by hackers because a user with administrator rights has permissions to install programs. Some users with administrator rights unknowingly allowed and continue to allow malware to be installed.
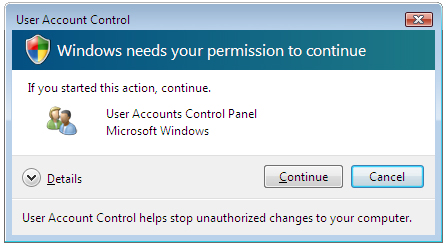
UAC Elevation Prompt
Vista has changed the user setup process to protect computers and networks from malware that exploited the default administrator rights that were applied to each new user. Vista assigns administrator rights to the first user that is set up. Every user after this is given standard rights by default, which do not contain permissions to install programs or change settings that effect all users.
Standard users will need to be manually changed to either an administrator level account or assigned one of the security group settings discussed above. Even administrators will have to deal with User Account Controls when a program is trying to be installed on a computer, or when settings that effect all users are being changed such as Windows firewall or Windows Updates.
User Account Control Panel
The UAC checks a users security token, which is assigned to each user during logon. The security token contains the users privileges and security group membership, and determines what the user can and cannot do. Events that cannot be accomplished with a standard account can be carried out if an administrator level account password is entered. Even if an administrator level user attempts to change certain settings, the UAC will display an Elevation Prompt message that will inform the user that the action is being requested, provide details, and the user can either click on the Continue or Cancel buttons.
This occurs because an administrator's token is actually a split token. One half includes standard user permissions and is used during logon and while using the computer. When higher level permissions are required, the administrator half of the token is accessed by clicking Continue on the UAC Administrator Approval Mode Elevation Prompt window. This provides another layer of security.
Permissions that standard and administrative users have by default include:
Standard |
Administrator |
|---|---|
| Changing time zones | Installing and uninstalling programs |
| Changing power management settings | Installing a device driver |
| Creating and configuring Virtual Private Network (VPN) connections | Installing Windows updates |
| Establishing a Local Area Network connection | Installing an ActiveX control |
| Adding printers | Changing firewall settings |
| Establishing and configuring a wireless connection | Changing the date and time |
| Establishing and configuring a Bluetooth device | Changing Parental Control settings |
| Restoring backed-up files | Adding, removing, and changing a user's account type |
| Synchronization with a mobile device | Changing Automatic Updates settings |
| Modifying display settings and desktop background | Changing UAC setttings with the Security Policy Editor |
| Playing and burning of CD or DVD media | Changing Remote Desktop access settings |
| Configuring battery power options for laptops | Schedule Automated Tasks |
| Configuring Accessibility options | Restore backed-up system files |
| Changing own password | Working with system files |
| Set up and use the Remote Desktop feature | Working with audit logs |
The UAC Elevation Prompt can be disabled by following the steps in the simulations below.
Events that prompt the UAC to display the Elevation Prompt can be changed from their default settings by using the local Security Policy Editor tool (secpol.msc) found by using the path: Local Security Settings-->Local Policies-->Security Options. Administrators Access Mode can even be changed to have to input their password for the Elevation Prompt.
Events that prompt an Elevation Prompt are color coded to be application specific. If the application publisher is blocked by a policy or Windows, a red window bar appears. A splash background bar signifies a Vista published application, while a Microsoft verified publisher prompts a grey bar window. An unsigned program prompts an orange bar window.